Taiwan & the internet during world war
Adapted from a talk at the U.S./Taiwan Science & Technology Cooperation Dialogue
This blogpost is adapted from my talk at the U.S./Taiwan Science & Technology Cooperation Dialogue in May, 2023.
A related update: My piece with Tejas Narechania, Inside the Internet, has been accepted into Duke Law Review! We discuss competition and concentration at the internet’s core. You can read a preprint at SSRN.
Update 10/27/2023. Some research from Bradley Huffaker et al (2023) has good news: Taiwan’s reliance on Chinese ISPs has decreased dramatically since Russia invaded Ukraine (see Section 6.2). This change is undoubtedly due to conscientious work throughout Taiwanese government and civil society.
May 24, 2026
It’s May 24, 2026. A manager at a Chinese telecom company gets an unexpected message: disconnect at 12:00:00.
This station—a so-called cable landing point—hosts an undersea cable, which connects China’s domestic internet to the rest of the world. Turning off the cable would disrupt international data flows—both headed toward China and headed from China to other countries.
The manager checks with her boss, who checks with his boss, all the way up the chain of command. The message is legitimate. She prepares to disconnect.
Managers at several cable landing points get similar messages. At noon, they flip their switches, and every landing point that serves Taiwan goes dark.

Within seconds, the internet begins to degrade in Taiwan. Websites don’t work. Nothing loads.
Within minutes, the internet slows dramatically in Europe and the United States. Service crawls along—when it works at all. Many sites become inaccessible.
News spreads. Headlines speak vaguely about a “massive cyberattack.” Worse, many people can’t even read those headlines—websites, including news sources like CNN and the New York Times, are inaccessible.
The internet is breaking for everyone, and few know exactly what’s happening. Rumors and misinformation spread. Anxiety intensifies.
People flock to the grocery stores and empty the shelves. There are runs on banks. The panic buying during the Colonial Pipeline ransomware incident—even during the onset of COVID-19—pales in comparison to the level of social anxiety and unrest.
Meanwhile, in China, the internet hums along as usual. People access their favorite apps as usual, unaware of the issues facing the internet internationally.
What just happened?
Is such a scenario possible? I’ll argue: yes.
In this post, I’ll explain how…
China can “cut” undersea cables without naval action.
Doing so would severely degrade the internet worldwide.
…but affect China relatively less.
China’s network topology implies that it is preparing for such a scenario.
I’ll then describe my three proposed remediations:
Short-term: The world should prepare wartime BGP routes.
Medium-term: Taiwan should invest in local networking infrastructure.
Long-term: Taiwan and its allies should prepare a trustworthy network of LEO satellite backlinks.
How is this attack possible?
Undersea cables—the physical network
Let’s start with the undersea cables.
There’s a line in the Tao Te Ching, 大制不割, often translated to English as: “the deepest cut cannot sever it.” We often think of the internet this way. We think of it as something impenetrably complex. A structure so decentralized that it cannot, as it were, be ‘severed.”

Unfortunately, the internet can very much be severed. The undersea cables that carry 99% of all the world’s internet traffic are physical, and cutting even a few of them would produce wide-ranging and long-lasting damage to the whole world’s internet.
We can represent the network of undersea cables as a network, or graph. I produced this network with some data analysis of my own.

As you can see, the U.S., highlighted in red, is very much the center of this undersea network. It is the fulcrum.
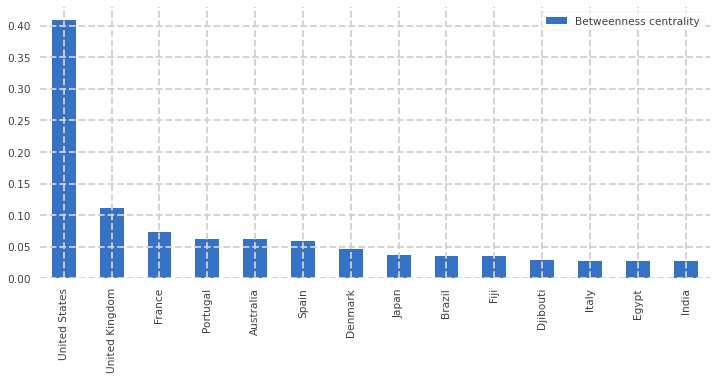
You won’t be surprised to learn that the U.S. has tremendous power over the network, serving as a “broker” for many other countries (for example: if Brazil wants to send a packet to Canada, they’ll frequently have to send those packets through the U.S.).
This ability to “broker” connections between other countries turns out to be an important part of the story here. Keep this idea in your back pocket as we continue.
Taiwan
Let’s see where Taiwan fits into this picture.
Here we see the cables connecting to Taiwan:
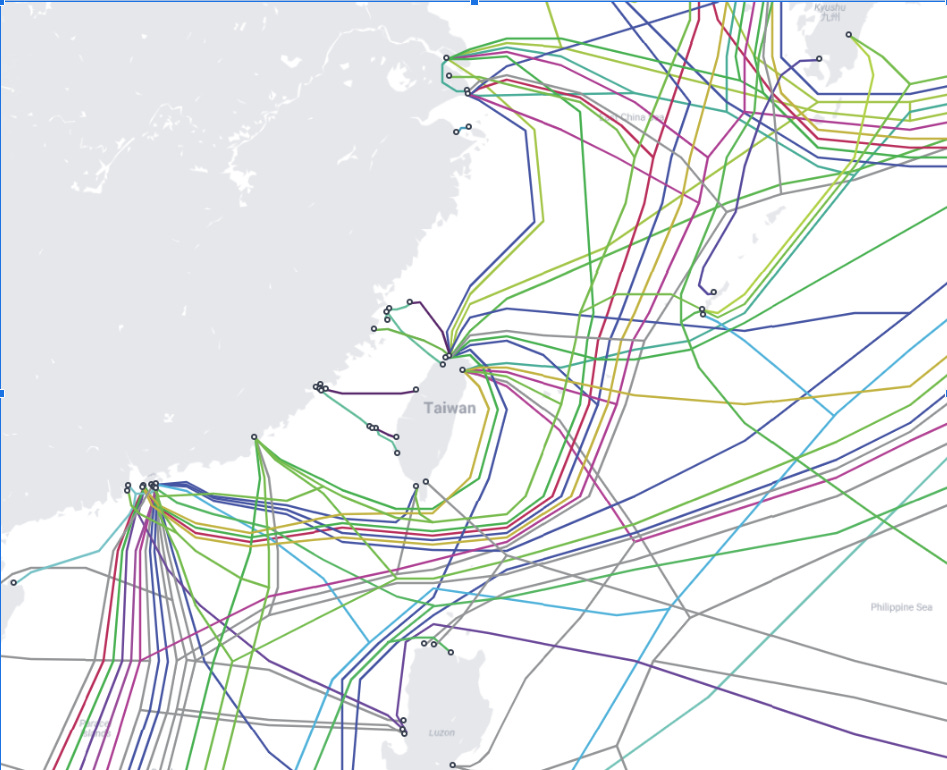
Here are those same connections represented as a subnetwork of our larger graph. These are all the countries to which Taiwan is connected by undersea cables:
Looking at this subnetwork alone, it seems counterintuitive that snipping these nine connections would have such an outsized effect. Wouldn’t the internet simply “route around the failure,” as internet evangelists were once so fond of saying? Taiwanese internet service providers should fall back on their relationships with Japanese, Korean, and Singaporean counterparts.
Unfortunately not. There are two, key reasons why this “fallback” isn’t as straightforward as it might seem.
First, the cables that China would cut to Taiwan also provide service to Japan, Korea, and Singapore. In the parlance of network analysis, four countries form a cluster—the cables that connect any two are also likely to connect the rest. Cutting one cuts the lot.
Second, the full story of internet connectivity in the region cannot be discerned by cable connectivity alone. Equally important is the logical network built on top of these physical cables.
The logical network
Undersea cables tell us about the physical network. On top of that physical network, there is a logical network - a software-defined network of peering relationships between autonomous systems, or ASs. This network is governed by the border gateway protocol or BGP. This network makes individual computers, like yours and mine, able to send and receive packets globally.
The question this network answers is: if some machine is requesting a packet from some other machine, who do they need to ask to find out how to get it?
As such, this network also allows us to ask the question: What happens when some particular route becomes unavailable?
At the physical layer, the answer is obvious. The cable is dark; no bits flow.
But what happens at the logical layer?
Local outages, global effects
To answer this question, let’s look to a historical example.

During Hurricane Sandy, a few routes in New York became inaccessible due to outages in local ISPs. This might be equivalent to ISPs in Taipei going offline.

The result of this outage was surprisingly severe and surprisingly widespread. We expect people in New York to have no service during this outage - their power is out. What was surprising is that the internet slowed down for almost everyone in the United States, and even for many people in far-flung places as Russia and Brazil.
Why?

To understand why a local outage had such global effects, let’s return to the logical network.
It turns out that data can sometimes take surprisingly international routes at the logical layer, even when that data’s origin and destination are within the same country.
Say you’re in Canada requesting data from somewhere else in Canada. You might expect that packet to stay in Canada. Right?
Actually, 45% of the time, that packet will travel to the U.S. while it’s on its journey (see A).
As we can see here, in most countries, requesting content in that country will take one of these “boomerang” routes.
And that’s only for domestic content. When we start to talk about packets that are bound for international destinations, these international connections only become more important.
This is why local outages can produce vast, cascading effects.
When a whole country goes offline, those effects could be magnified even further.
Recall the U.S.’s high brokerage graph from earlier. The U.S. has a high brokerage with other countries—many other countries rely on it. This brokerage relationship is a double-edged sword: it means other countries rely on the U.S. to get their messages to the world.
Say Taiwan becomes suddenly unavailable. Now, all of the packets that the world tries to send to Taiwan start to pile up… in the U.S.!
The U.S. has to update many, many routes to heal the network. This healing happens by passing BGP messages—which further add to the congestion, not just in the U.S., but worldwide.
That congestion makes the internet slow for everyone. Switchboard queues start to overflow. Devices fail. That causes outages in U.S. routes, which cause congestion in other routes, which fail over and cascade globally. You get the idea.
China’s network sovereignty
Fine. But why doesn’t this affect China? Sure, this attack is globally disruptive. Wouldn’t it also severely degrade China’s internet?

Unfortunately not.
Amazingly, and very cleverly, China has carefully architected its domestic internet precisely to withstand such an attack. As you can see from this “D” diagram, China-to-China routes don’t rely on the rest of the internet at all. 100% of domestic packets stay within the country.
How did China manage this?
Well, China has exactly zero non-domestic carriers operating domestically. That means the CCP has as much control over domestic internet routing as they’d like to have:
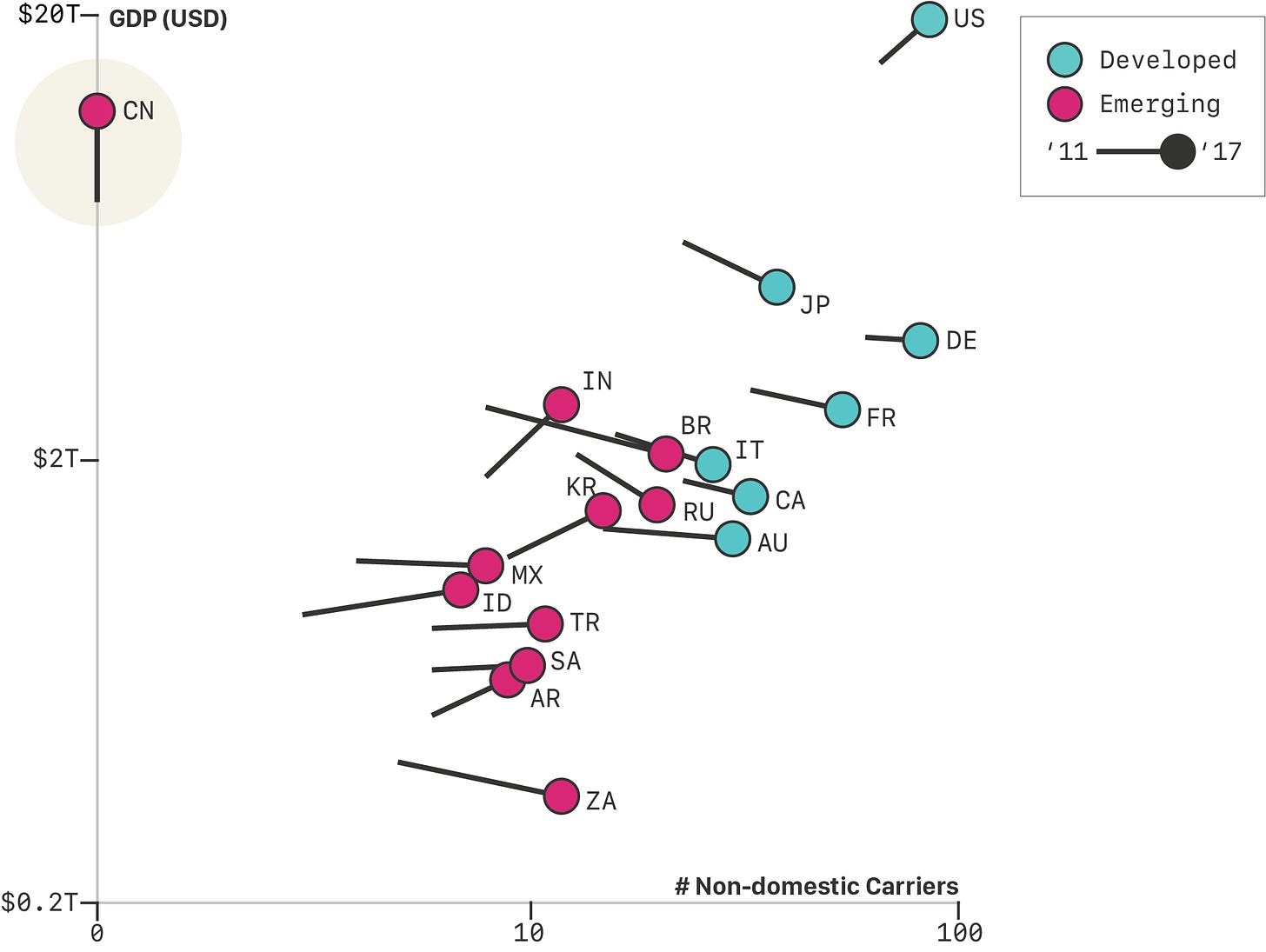
So, China has a network that can act like a country-wide internet in case it wants to withdraw from the global network.
So an attack on international internet infrastructure won’t affect China’s domestic internet. But surely it would affect China’s ability to send packets internationally, right?

Maybe. But, again, China has done something clever. They’ve produced a national “bottleneck,” which makes international data transfer much slower than domestic data transfer.
This bottleneck confers two, key advantages to China.
First, a single bottlneck makes it easier for China to cut itself off from the global internet if it ever needs to - in the case of an attack on its domestic infrastructure, or in the case it wants to attack global internet infrastructure, as we’ve described.
Second, as the authors of this study point out, this bottleneck subtly trains people in China to prefer domestic content providers. Domestic websites simply perform better than international ones.
If the rest of the internet became inaccessible, people in China might notice — if they use foreign apps. However, they probably don’t. Website popularity data indicates that people in China already prefer to use China-domiciled apps and infrastructure.
Side note: We can imagine China tweaking the parameters of this bottleneck to exacerbate the latency of international apps and websites even further. That would exacerbate domestic preferences for domestic apps and service providers. Indeed, if we ever observed this bottleneck becoming more severe, it could indicate that an attack is imminent.
Where do we stand?
So:
China can “cut” undersea cables without naval action.
Doing so would severely degrade the internet worldwide.
…but affect China’s domestic internet relatively less.
China’s network topology implies that china has prepared for such a scenario.
What do we do about it? How do we even out this asymmetry?
What do we do?
Short-term: Wartime BGP routes
First, the world should prepare “wartime routes.”
These routes should be on-the-books backup routes in case Taiwan, or other countries, become unavailable during times of war.
Being able to “flip over” to these pre-prepared routes will dramatically reduce congestion. This will mitigate global congestion in a wartime scenario - in the scenario in which U.S. or other global internet congestion comes out of control.
Medium-term: Local networks

Second, Taiwan should invest in backup, local infrastructure that routes densely domestically. Mesh networks, working rooftop-to-rooftop, like the one seen here, in New York City, are especially well-suited to Taiwan’s dense cities. These networks can provide a critical backup in the event of wonky local infrastructure.
Another wonderful thing about mesh networks is that they’re hard for attackers to turn off. Even during a full-scale land invasion, it would be hard to disconnect this network completely. I talked with Dr. Shin-ming Cheng yesterday about how difficult it was for the police to find a malicious cell tower in Taiwan. Imagine that situation times one hundred, and that’s how hard it would be to take down one of these mesh networks.
Using microwave or radio links, a point-to-point mesh could extend across the Pacific. It might be possible to build a microwave network across a chain of islands (for example, to nearby Japanese islands, and onward to Japan).
Add a few satellite backlinks to this network, and Taiwan’s domestic internet could remain relatively stable even during a comprehensive cable-cutting attack. Which brings me to my final point.
Long-term: LEO satellite internet

The ultimate defense against cable-cutting attacks is a reliable and performant satellite internet network.
You’ve probably been waiting for me to mention this.
I used to be a skeptic about satellite internet, primarily due to concerns about latency, but a 2018 paper by Mark Handley convinced me that a low-earth orbit array could provide relatively robust and low-latency service.
Quoting from the paper:
“…a network built in this manner can provide lower latency communications than any possible terrestrial optical fiber network for communications over distances greater than about 3000 km.” (Handley, 2018).
Now, you might be thinking: isn’t this how Starlink works? Why is this in the “long-term” category?
I place an LEO satellite internet in the long-term category for two reasons.
First, this satellite array needs to be dense. To replace a severe submarine cable outage, we would need many more satellites than Starlink has.
Second, Starlink can only be trusted insofar as the people who manage that network can be trusted. (This is a pervasive problem in internet stability overall: the infrastructure that runs the internet may be decentralized, but the management of that infrastructure is highly concentrated, usually in the hands of one or two people. I’ve written and researched extensively on this problem.).
In this case, Taiwan can only trust Starlink insofar as it can trust Elon Musk. So, it cannot trust Starlink at all.
Taiwan needs an LEO satellite internet provider it can trust in combat. Nationalizing Starlink is not a crazy idea. Nor is it crazy for the Taiwanese government, ASEAN, or some consortium of bodies to collaborate on building an LEO network. Even a regional network in the Indo-Pacific might do - this network only needs to cover areas that are likely to experience cable faults.
Final thoughts
What did we learn?
China is ready to perform attacks on “common” internet infrastructure
These attacks will hurt us more than they will hurt China.
Countermeasures:
Prepare wartime routes
Invest in mesh networks in Taiwan
Build trusted LEO satellite network infrastructure
In the internet, we should find an example of weaponized interdependence: the U.S. has a central role in the whole of the internet, and might leverage that position for asymmetrical advantages. Instead, we find an inverse of weaponized interdependence: China is weaponizing the fact that some other actor has in a central role in the network, and introduces asymmetries to make that centrality more painful than the central actor initially expected.
I gave this talk two days before news broke that a Chinese APT had compromised critical infrastructure in Guam, apparently with the intent to disrupt communications. Some journalists speculated Taiwan was the “real target.”
The real target is bigger than Taiwan—and bigger than Guam. The U.S. “holds” the Pacific. China would prefer it “held” the Pacific. Chipping away at the infrastructure that makes an internet out of that ocean is important—but it’s also just one plotline in a complex strategic drama.
But this drama is larger than who “holds” the Pacific. The U.S. “holds” the mechanisms of commerce—the internet, financial systems—the machinery of the world. Perhaps the internet is one domain where China’s ability to weaponize interdependence has outpaced the West. A bit, for now.
This work was funded in part by grants from the Internet Society and the William and Flora Hewlett Foundation.
Thanks to Akhilesh Pandita, Amreesh D. Phokeer, Ashwin Mathew, Cristian Alamos, Chris Hoofnagle, Andrew Reddie, and Zachary Bischof for their help with this research.
Thanks to Yih-Chun Hu, Hsu-Chun Hsiao, Ying-Dar Lin, and Yuh-Jye Lee for their thoughtful comments, and to Taiwan’s Ministry of Digital Affairs for inviting me to speak.






Nice to see you present today!
Curious what you make of this. Will all this money just get siphoned off at the top, or is there a chance this makes any difference?
https://apnews.com/article/biden-internet-broadband-bead-0b95fabd7f6833ce420c80d474a145a5