I’m a researcher at the UC Berkeley Center for Long-Term Cybersecurity where I direct the Daylight Lab.
I’ve mentioned DAOs many times on this blog. In fact, I’ve been working on DAO DAO, a DAO that builds DAOs. (Try it out—we’re in beta). But, what is a DAO?
This post is part of a series.
Background: This Internet, on the Ground
Part 1. Governable internets
Part 2. How governance could be
→ Part 3. What are DAOs?
Part 4. An internet of DAOs
Part 5. Identity bureaus
Part 6. But can it govern?
Part 7. Pockets of liberation
Defining DAOs
DAOs. What a word! It reminds me of the Tao Te Ching. (See Ursula Le Guinn’s translation).
The way DAOs are often explained is as ambiguous and ethereal as descriptions of the internet were in the 1990s. DAOs are a sociotechnical system for which no great analogies exist. A corporation is one analogy—corporations have voting shares, which are like governance tokens.
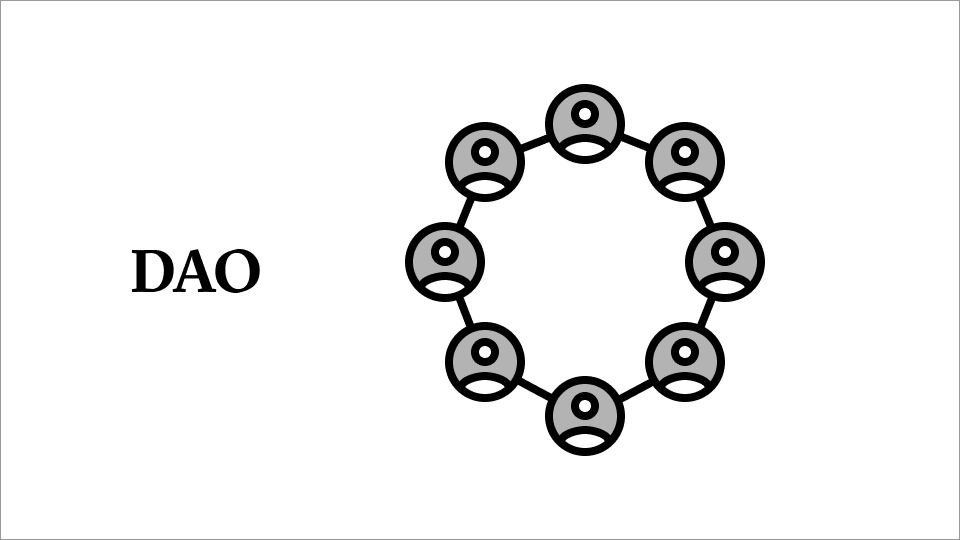
At a high level, DAOs are collectively owned governance systems cryptographically bound to obey the democratic wishes of token holders.
Let’s decompose this definition. We’ll do so from “high” to “low.” we’ll start at this most abstract layer, and descend its technological “stack” until we can see DAOs as material.
A governance system
A DAO is a governance system. It is a system by which rules can be made. It is a group of people who believe in those rules.
Ah, “who believe in those rules.” Yes, they are people who consent to be governed. This is a group that believes its system’s rules are legitimate, that the rules by which those rules can be changed are legitimate.
In other words, a DAO is collectively owned. It is a group of people who will make rules together.
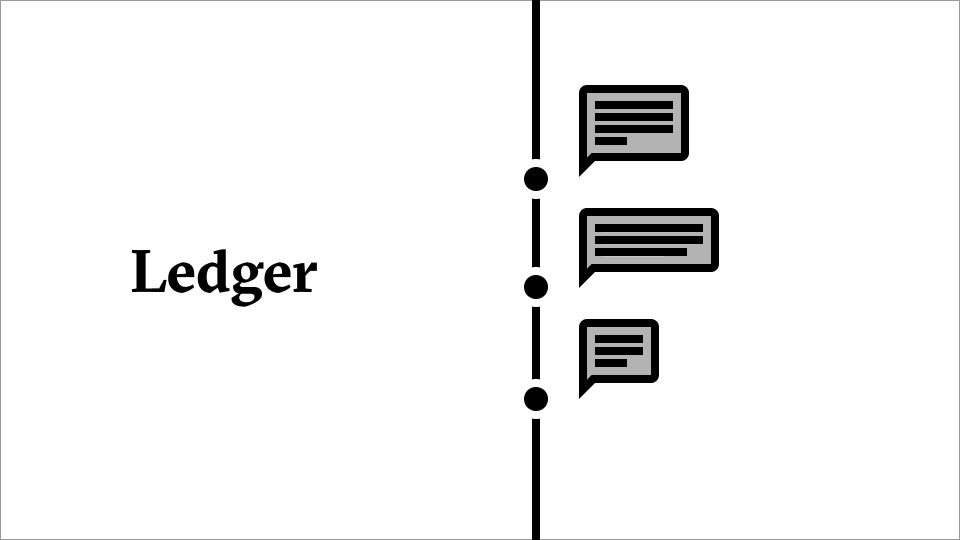
A record; a ledger
Their goal is to construct a series of rules. A ledger. Effectively, a timeline, where each entry is an event that occurred in the governance system. So and so proposed to do such and such. So and so voted. The proposal passed.
The rules they pass can be human-readable, like laws.
Or they can be machine-readable, like code. Indeed, we can use the governance system to update one or many software systems collaboratively. We can even run those software systems on some blockchain to confirm that the software is being run the way we governed it to be.
The cryptography of it all
How does this system work? How can we make a governance system that’s cryptographically bound to obey itself?
Let’s start with the single person, the atomic individual.
This notion of an atomic individual is an interesting one. It’s fun to pluck and prod at. What is it about natural-born personhood that makes it so easy to assign rights and privileges? We have this notion of an individual with deep traditions in the Enlightenment, all of Western law.
If we want to do something in software we must—always, necessarily—make specific epistemic commitments about who this “user” is, this person, this individual. The way we’ll do it in our system is simple, almost so simple as to be laughable when you say it out loud.
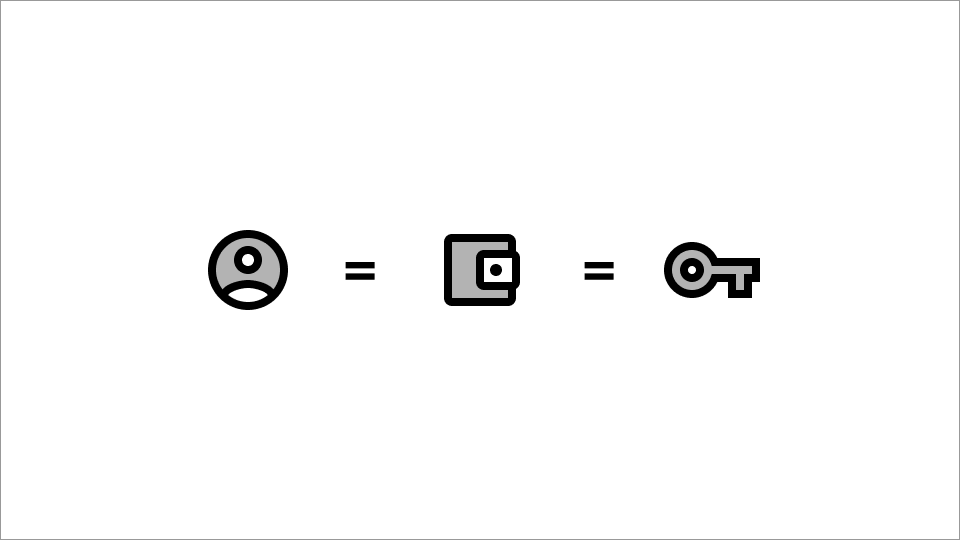
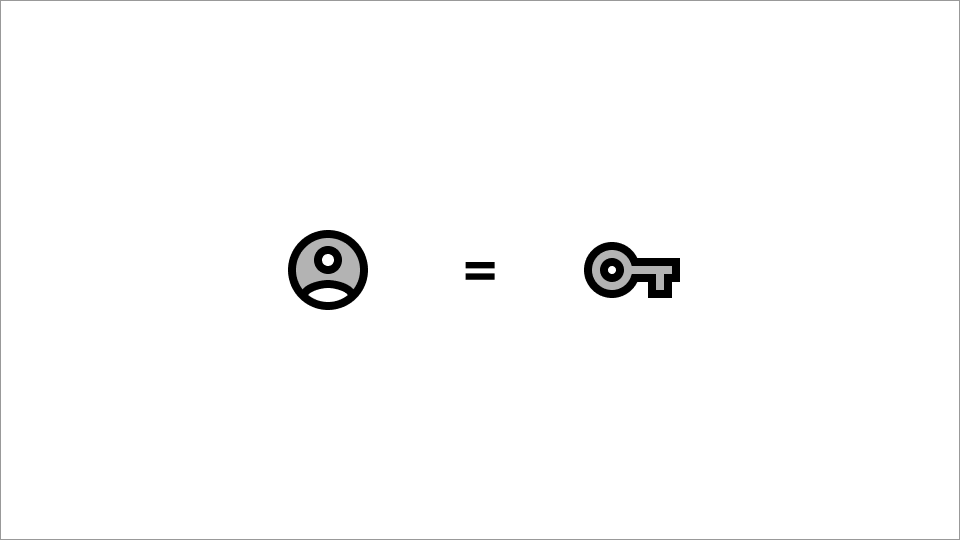
We represent users as a wallet.
Wallet = keypair
A wallet is a pair of cryptographic keys, along with a few methods for using them (signing things, encrypting things, decrypting things).
Keys have a public and secret part. Your public key is globally known. They are public. They are, in the parlance of DAOs, your address. Secret keys are known only to you. They are kept secret to everyone but you.
With this keypair (as it’s known), you can sign things. You can prove that you (someone with control of your wallet) “authorized” or “approved of” something, like a public transaction, without revealing your secret key.
This wallet, and the ability of that wallet’s user to perform these actions, enable this individual to participate in governance in the DAO. A legal transaction (one the blockchain allows, such as transferring tokens you own) that has your signature on it will be “executed:” placed on the blockchain forever.
User = keypair
So the user, this person, is a set of cryptographic keys.
It’s okay to laugh at this! It’s an absurd proposition on its face. A living, breathing person is more than a set of keys!
Of course. We are more than keys. These keys represent us. In doing so, they represent us as a reasoning individual who can protect and use these keys. We—that individual—are that thing that can manage a pair of keys - that reasoner, that thing to whom personhood is granted.
You can see, a lot of assumptions are built into this formulation!
I call this formulation, this social idea, that an individual can be represented by a pair of cryptographic keys cryptographic personhood. You can read more about it there.
Tokens
For now, let’s return to the DAO. An organization of cryptographic persons.
DAOs can create tokens.
Tokens are an atomic unit of scarcity. They can be subdivided in arbitrary ways, or not. They can all be alike, or each can be unique. (That is, they can be fungible or non-fungible, respectively).
What matters about tokens is this: there is some finite number of them in existence at any given time. The ledger, plus your control over your private keys, determines your ability to control the tokens that the ledger says you own. If the ledger says your wallet owns some tokens, you and you alone can move those tokens, transfer them, and so on.
In the context of a DAO, tokens typically determine your voting share.
Programmable units of scarcity
Tokens, being software, are programmable. You might be forbidden from transferring them. Perhaps tokens can only be moved around by popular vote. And so on, and so on. This idea of a token is very flexible—they enable rich applications to be built on top of them.
These applications can take any number of forms. Cryptocurrencies were the token’s original and most obvious application. But they can also apply notions of ownership to something intangible, such as “owning” a piece of art - an abstract concept, one divorced from having made the piece, that maps imperfectly to the notion of other people agreeing that you own it.
They can, in our case, grant rights—they can determine your voting share, or perhaps serve to authenticate you, to grant you access to services.
They could authenticate you, for example, to an ISP, who will, in turn, connect you to an internet.
We’ll talk about that next time.
Thank you for reading. This blog is free without a subscription thanks to my delegators. To support my work, delegate to elsehow on Juno or Stargaze.w






Extremely well written. I may try my hand at creating one, even just for the learning experience.